As I was searching for some EKS documentation, found this Link and thought, lets quickly connect K8's running in my HomeLab to EKS for fun. I thought it would be a quick few commands from AWS and done with it. But for some reason the documentation specially on default connector role have issues with SSM access, I have to spend some time to come up with working list of commands and thought it would be better to install with a custom connector role.
I then took this as opportunity, and created a script to make this automated, each of the task from this script can be taken as an individual step.
PreReq:
- Connect to HomeLab k8 in terminal
- Also have that terminal authenticated to AWS (Admin Access, to make it simple)
Steps part of script:
- Create custom eks connector policy and role
- Register Cluster that need to be connected with a name and connector role
- Install eks-connector helm in k8 cluster
- Apply cluster roles for the IAM Role that requires access to this Cluster in AWS
eks-connector-script.sh
#!/bin/bash
# Set variables from user input
AWS_REGION=$1
IAM_ROLE_ARN=$2
CONNECTOR_ROLE_NAME=$3
K8_CLUSTER_NAME=$4
# Create custom connector role
OUTPUT=$(aws iam create-role --role-name ${CONNECTOR_ROLE_NAME} --assume-role-policy-document '{"Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Principal": { "Service": "ssm.amazonaws.com" }, "Action": "sts:AssumeRole" }]}')
echo $OUTPUT
eks_connector_arn=$(echo $OUTPUT | jq -r '.Role.Arn')
echo $eks_connector_arn
# Create and attach policy to connector role
OUTPUT=$(aws iam create-policy --policy-name ${CONNECTOR_ROLE_NAME}-SSMEKSConnectorPolicy1 --policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SsmControlChannel",
"Effect": "Allow",
"Action": [
"ssmmessages:CreateControlChannel"
],
"Resource": "arn:aws:eks:*:*:cluster/*"
},
{
"Sid": "ssmDataplaneOperations",
"Effect": "Allow",
"Action": [
"ssmmessages:CreateDataChannel",
"ssmmessages:OpenDataChannel",
"ssmmessages:OpenControlChannel"
],
"Resource": "*"
}
]
}' --query 'Policy.Arn' --output text)
###
aws iam attach-role-policy --role-name ${CONNECTOR_ROLE_NAME} --policy-arn $OUTPUT
sleep 5
while true; do
POLICIES_ATTACHED=$(aws iam list-attached-role-policies --role-name ${CONNECTOR_ROLE_NAME} | jq -r '.AttachedPolicies[] | .PolicyArn')
if [ "${POLICIES_ATTACHED}" == "" ]; then
sleep 5
else
break
fi
done
# Register k8 cluster
output=$(aws eks register-cluster --name ${K8_CLUSTER_NAME} --connector-config provider=OTHER,roleArn=${eks_connector_arn} --region ${AWS_REGION})
# Extract activation ID and code from output
ACTIVATION_ID=$(echo $output | jq -r '.cluster.connectorConfig.activationId')
ACTIVATION_CODE=$(echo $output | jq -r '.cluster.connectorConfig.activationCode')
# echo $ACTIVATION_ID
# echo $ACTIVATION_CODE
# Get ECR public login password and docker login
aws ecr-public get-login-password --region us-east-1 | docker login --username AWS --password-stdin public.ecr.aws
# Install eks-connector
helm install eks-connector \
--create-namespace \
--namespace eks-connector \
oci://public.ecr.aws/eks-connector/eks-connector-chart \
--set eks.activationCode=${ACTIVATION_CODE} \
--set eks.activationId=${ACTIVATION_ID} \
--set eks.agentRegion=${AWS_REGION}
status=$(helm status eks-connector -n eks-connector | grep "STATUS:" | awk '{print $2}')
echo "Checking helm install status ......."
sleep 4
# Check if the status is deployed
if [ "$status" == "deployed" ]; then
echo "Deployment completed. Running next steps..."
curl -O https://s3.us-west-2.amazonaws.com/amazon-eks/eks-connector/manifests/eks-connector-console-roles/eks-connector-clusterrole.yaml
curl -O https://s3.us-west-2.amazonaws.com/amazon-eks/eks-connector/manifests/eks-connector-console-roles/eks-connector-console-dashboard-full-access-group.yaml
sed -i.bak "s|%IAM_ARN%|${IAM_ROLE_ARN}|g" eks-connector-clusterrole.yaml
sed -i.bak "s|%IAM_ARN%|${IAM_ROLE_ARN}|g" eks-connector-console-dashboard-full-access-group.yaml
kubectl apply -f eks-connector-clusterrole.yaml
kubectl apply -f eks-connector-console-dashboard-full-access-group.yaml
fi
# Run the next steps only when the deployment is complete
echo "Completed."
Run:
chmod +x eks-connector-script.sh
./eks-connector-code.sh <aws_region> <iam_role_arn> <connector_role_name> <k8_cluster_name>Example to connect and provide AWS SSO Role access:
./eks-connector-code.sh us-west-2 arn:aws:iam::1234567890:role/AWSReservedSSO_AWSAdministratorAccess_21783f33dd eks-connector-role-custom homelab-k8sScreenshot once Connected:
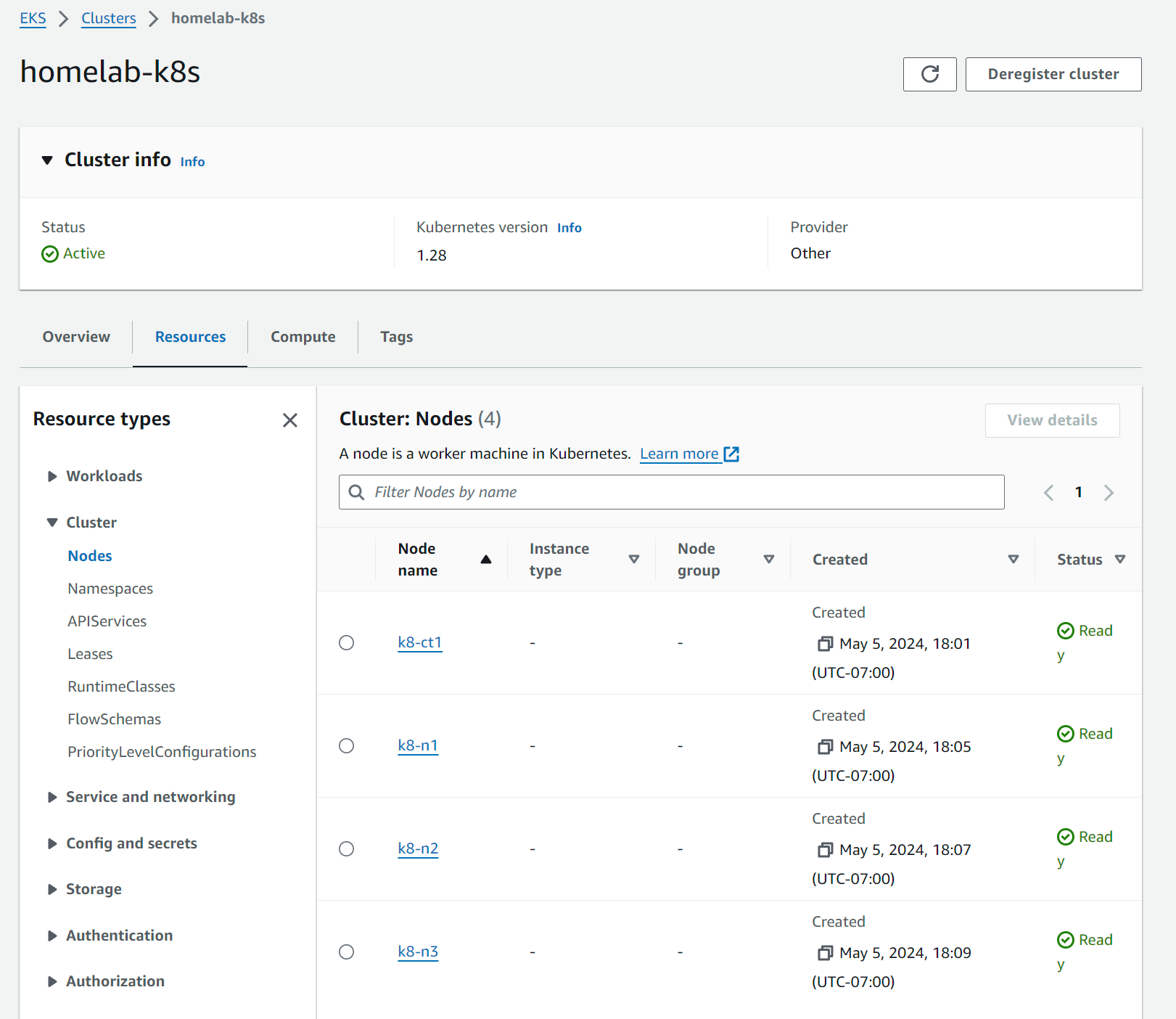
Uninstall:
kubectl delete -f eks-connector-clusterrole.yaml
kubectl delete -f eks-connector-console-dashboard-full-access-group.yaml
helm uninstall eks-connector -n eks-connector
aws eks deregister-cluster --name homelab-k8s --region us-west-2Ref/Notes: